Digital wallet architecture forms the backbone of modern cryptocurrency interactions. Furthermore, understanding how wallets manage keys and process transactions becomes essential for developers and users alike. This comprehensive guide explores the fundamental components that make secure digital transactions possible.
Modern wallet architecture encompasses several critical elements that work together seamlessly. Moreover, these systems handle everything from key generation to transaction broadcasting while maintaining security standards. Additionally, proper wallet design ensures users can safely store and transfer digital assets.
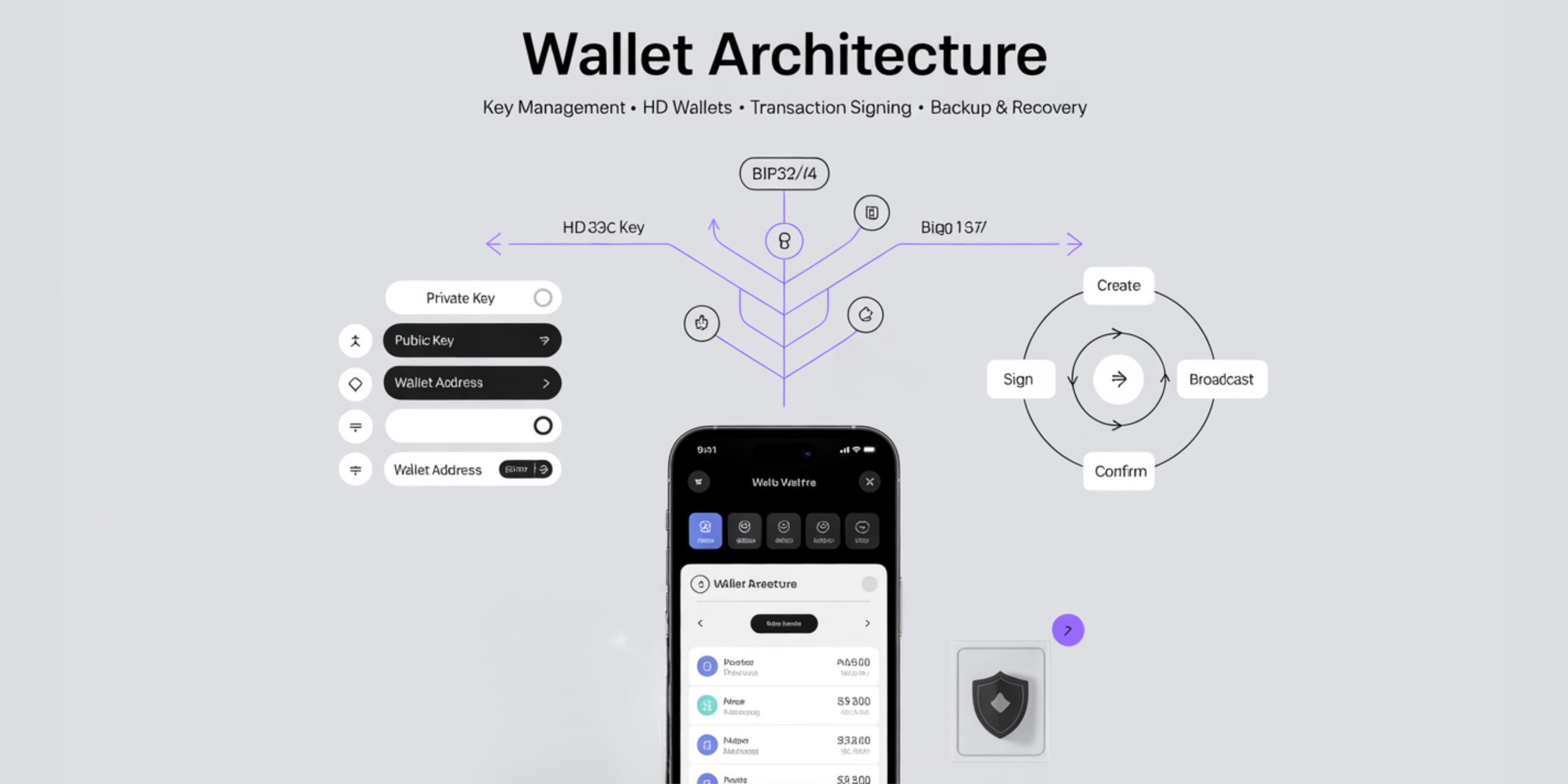
Key Management: Private Keys, Public Keys, and Address Generation
Key management represents the most crucial aspect of wallet architecture. Specifically, wallets generate and store cryptographic keys that control access to digital assets. Cryptographic key generation follows established mathematical principles to ensure security.
Private keys serve as the master password for wallet access. These randomly generated numbers must remain secret and secure at all times. Consequently, anyone with access to private keys can control the associated digital assets. Private key security requires careful implementation and storage practices.
Public keys derive mathematically from private keys using elliptic curve cryptography. However, this process works only in one direction, making it impossible to reverse-engineer private keys. Therefore, public keys can be shared safely without compromising wallet security. Elliptic curve cryptography provides the mathematical foundation for this security model.
Address generation transforms public keys into user-friendly wallet addresses. Subsequently, these addresses serve as destinations for receiving digital assets. Most importantly, addresses undergo hashing processes that add additional security layers. Address generation algorithms vary between different blockchain networks.
The relationship between these components creates a secure hierarchy:
- Private keys enable complete wallet control
- Public keys verify transaction authenticity
- Addresses provide safe sharing mechanisms
Hierarchical Deterministic (HD) Wallets: BIP32/44 Standards and Key Derivation
Hierarchical Deterministic wallets revolutionized key management through standardized derivation processes. Initially, BIP32 specification introduced the concept of deriving multiple keys from a single seed. Furthermore, this approach eliminates the need to backup individual keys separately.
HD wallets generate an entire tree of keys from one master seed. Consequently, users only need to backup the initial seed phrase to recover all addresses. Additionally, this system enables organized key management through hierarchical structures. Key derivation standards provide consistent implementation guidelines across different wallet providers.
The BIP44 standard extends BIP32 functionality by defining specific derivation paths. Specifically, it establishes rules for organizing keys by purpose, coin type, account, and address index. Therefore, wallets can support multiple cryptocurrencies within a single hierarchical structure. BIP44 implementation ensures compatibility between different wallet applications.
Key derivation follows a mathematical process that generates child keys from parent keys. Moreover, this process can create both hardened and non-hardened derivation paths. Hardened derivation provides additional security by requiring the parent private key for child key generation. Hardened key derivation prevents unauthorized key generation even with parent public keys.
The derivation path structure follows this format:
- m/44’/0’/0’/0/0 represents the first Bitcoin address
- Each level serves specific organizational purposes
- Apostrophes indicate hardened derivation steps
Transaction Signing: Creating and Broadcasting Transactions
Transaction signing demonstrates the practical application of wallet architecture principles. Initially, wallets construct transaction data containing sender, receiver, and amount information. Subsequently, this data undergoes digital signing using the sender’s private key. Digital signature algorithms ensure transaction authenticity and non-repudiation.
The signing process creates a mathematical proof that the transaction originator possesses the private key. Furthermore, this proof allows network participants to verify transaction validity without accessing private keys. Additionally, signed transactions become immutable records that cannot be altered without detection. Transaction verification protocols enable trustless network operations.
Transaction broadcasting distributes signed transactions across the blockchain network. Consequently, network nodes validate and include these transactions in blocks. Moreover, proper broadcasting ensures transactions reach sufficient network participants for processing. Network propagation mechanisms handle transaction distribution efficiently.
Wallet architecture must handle various transaction types and formats. Specifically, different blockchain networks implement unique transaction structures and signing algorithms. Therefore, multi-currency wallets require specialized handling for each supported network. Multi-chain wallet development presents additional architectural challenges.
The complete transaction flow includes these steps:
- Transaction construction with inputs and outputs
- Digital signing using appropriate private keys
- Network broadcasting through peer-to-peer protocols
- Confirmation tracking and status updates
Backup and Recovery: Seed Phrases, Key Storage, and Security Best Practices
Backup and recovery mechanisms protect users from permanent asset loss. Primarily, seed phrases serve as human-readable backups for HD wallet master seeds. Furthermore, these phrases typically consist of 12 or 24 words selected from a standardized dictionary. BIP39 mnemonic specification defines the seed phrase generation process.
Seed phrases enable complete wallet restoration on any compatible device. Additionally, proper seed phrase storage becomes critical for long-term security. However, physical storage methods often provide better security than digital alternatives. Hardware wallet security offers enhanced protection for seed phrase storage.
Key storage security requires balancing accessibility with protection from threats. Moreover, encrypted storage solutions protect keys from unauthorized access while maintaining usability. Additionally, multi-signature architectures distribute key control across multiple parties. Multi-signature wallet implementation reduces single points of failure.
Security best practices encompass both technical and operational considerations. Specifically, regular backup verification ensures recovery mechanisms function correctly. Furthermore, secure key generation requires proper random number generation and entropy sources. Cryptographic random number generation provides the foundation for secure key creation.
Advanced security measures include:
- Air-gapped key generation and storage
- Time-locked recovery mechanisms
- Social recovery through trusted contacts
- Regular security audits and updates
Wallet architecture continues evolving as new security challenges emerge. Subsequently, implementing robust backup and recovery systems protects against both technical failures and user errors. Therefore, comprehensive security planning should address all potential failure scenarios.
FAQs:
- What makes HD wallets more secure than traditional wallets?
HD wallets generate all keys from a single seed, eliminating the need to backup multiple private keys. Additionally, they support hierarchical organization and enable advanced security features like hardened derivation paths. - How do seed phrases work for wallet recovery?
Seed phrases represent the master seed in human-readable format. Consequently, entering the correct seed phrase into any compatible wallet recreates the entire key hierarchy and restores access to all addresses. - What happens if someone gains access to my private key?
Private key compromise grants complete control over associated digital assets. Therefore, immediate asset transfer to a new, secure wallet becomes essential. Furthermore, the compromised key should never be used again. - Can I use the same wallet architecture for different cryptocurrencies?
Yes, HD wallets support multiple cryptocurrencies through different derivation paths. However, each cryptocurrency may require specific implementation details and signing algorithms. Multi-currency wallet standards provide guidance for implementation. - How often should I backup my wallet?
HD wallets require only one backup of the seed phrase since all keys derive from it. However, regular backup verification ensures the recovery process works correctly. Additionally, backup security practices recommend secure physical storage methods. - What’s the difference between hot and cold wallet architectures?
Hot wallets maintain internet connectivity for convenient transactions but face greater security risks. Conversely, cold wallets remain offline, providing enhanced security at the cost of reduced accessibility. Cold storage solutions offer maximum protection for long-term holdings. - How do multi-signature wallets enhance security?
Multi-signature wallets require multiple private keys to authorize transactions, distributing control among several parties. Consequently, this architecture prevents single points of failure and enables shared custody arrangements. Multi-sig implementation provides additional security layers.
Stay updated with our latest articles on https://fxis.ai/